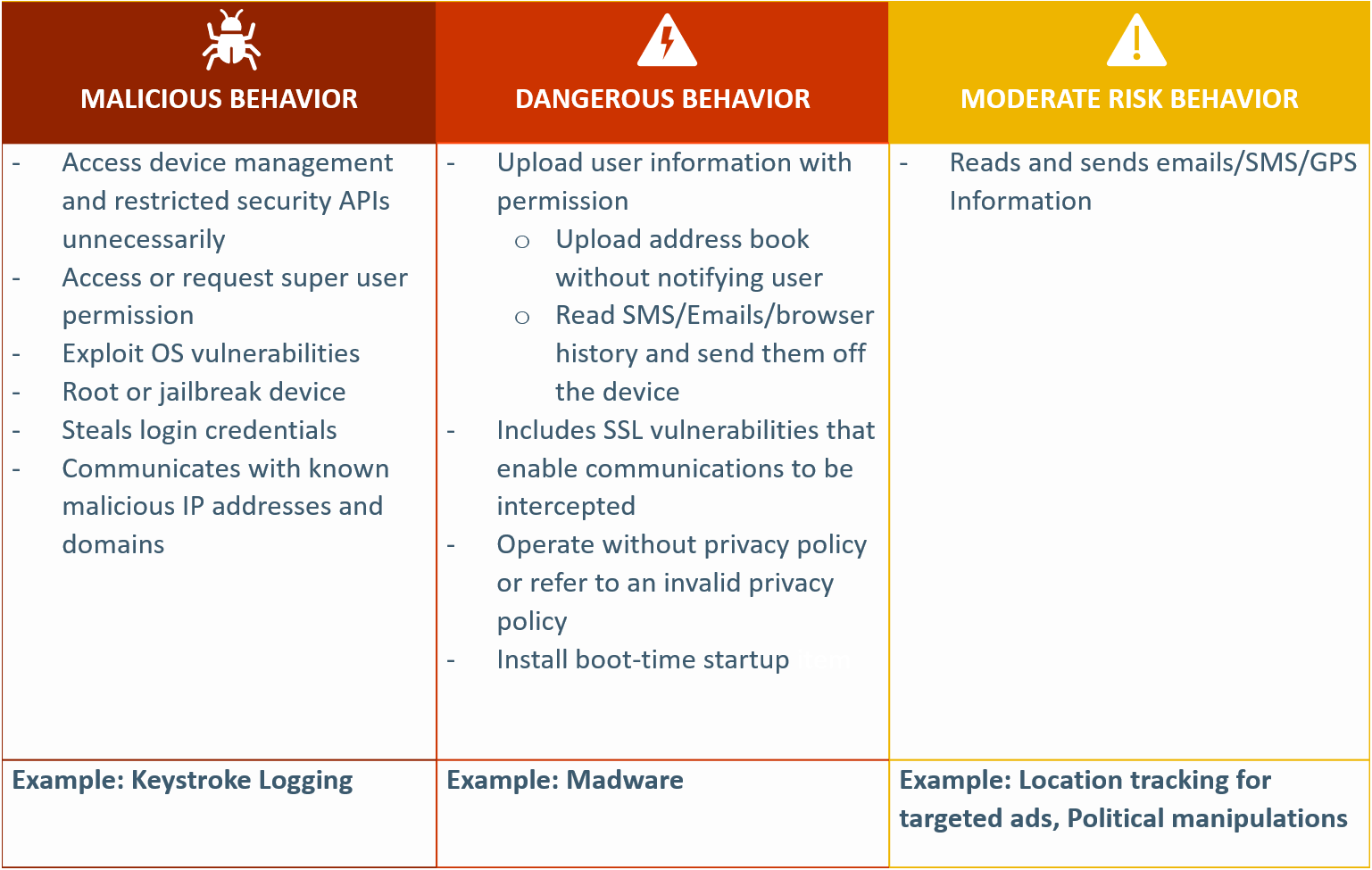
In the last two posts, we explored how some mobile apps were malicious in nature and indulged in stealing your personal data for their gains. We also looked at a few steps that mobile app developers can undertake to bring stronger, more resilient mobile apps that don’t support dangerous activities of hackers.
In this final part, we will understand what you as an end user can do to stay vigilant and prevent mobile apps from stealing your personal data.
Note to end users – How to hackproof your smartphone
Fingerprints can be lifted. Use passcode
One of the biggest nightmares for an individual these days is losing their phone. While the hardware must have cost big bucks, what’s more vital is the loss of personal data that’s present – think emails containing sensitive information, photos, videos and more. While most of us secure our phones with fingerprints, it is not always safe as it is easy to lift prints. It is better to use strong passcodes. And if you have an evil twin, it is time to say goodbye to facial recognition as an unlocking medium as well.
Also, while smart unlock features such as unlocking phone when you reach home/office is cool, it is dangerous when your phone is in the wrong hands.
Activate Find My Device feature so that even if physically lost, phone can be locked or wiped
Another way to proof your data in the event you have lost your device is to track it online and lock it. You can even wipe it fully so that the hackers cannot glean anything from it. In Android, Find My Device helps to locate the device as well as lock it or wipe it. iPhone users can use Find my iPhone feature to locate their devices and even switch on Lost Mode.

Don’t reveal sensitive data while on Public WiFi
Never use Public WiFi to perform financial or business transactions as hackers can position themselves between you and the connection point and intercept sensitive personal and corporate data. Always use secure connections while performing such activities. According to a Kaspersky Lab report, one in five persons has been a target of cybercrime while abroad and a third (31 per cent) of them are senior business managers.

Review app permissions and EULA before installing
It is important to review what all permissions an app is requesting before completing installation. As said before some apps seek permissions for internet and location just to send targeted ads and make money. And before you know it, your phone is filled with unwanted ads.
While mobile apps have been a boon to smartphone users around the world, the security risks associated with them cannot be denied. It is in your own personal interest that you monitor your apps and eliminate those that you think might compromise your data’s safety. Also, lesser the number of apps and lesser the number of distractions, the more organized your phone and well-spent is your time.