Microsoft Security Copilot: Overview
Cybersecurity is crucial to any business, especially in the digital age. However, managing security risks and threats can be challenging and time-consuming. That’s why Microsoft has developed Security Copilot, an AI-powered tool that helps you protect your data and devices from cyberattacks.
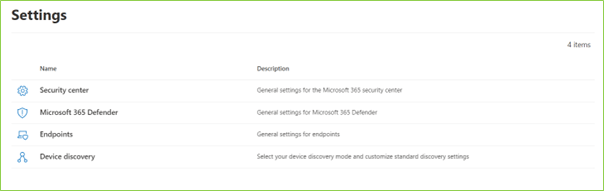
Security Copilot is a cloud-based service that integrates with Microsoft 365 and Azure. It provides you with a comprehensive and personalized security dashboard where you can monitor your security posture, identify vulnerabilities, and take action to remediate them. Security Copilot also leverages AI to analyze your security data and provide insights and recommendations on improving your security.
Features and Benefits
Some of the features and benefits of Security Copilot are:
- Gives you a single view of your security status across your Microsoft products, services, and third-party applications and devices.
- Alerts you of any security incidents or anomalies and helps you investigate and respond quickly and effectively.
- Uses AI to prioritize the most critical security issues and suggest the best actions.
- Helps you comply with industry standards and regulations, such as GDPR, HIPAA, PCI DSS, etc.
- Enables you to create and enforce security policies and controls across your organization.
- Allows you to customize your security settings and preferences according to your needs and preferences.
Getting Started with Microsoft Security Copilot
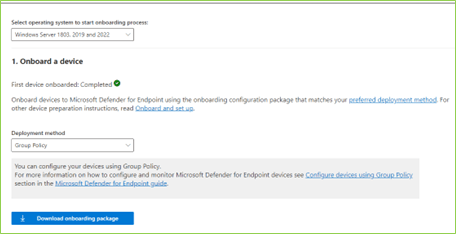
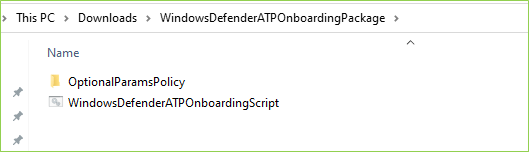
To use Security Copilot, you need to follow these steps:
- Sign up for a free trial or a paid subscription on the Microsoft Security Copilot website.
- Connect your Microsoft 365 account to the service using the Azure Active Directory (AAD) authentication.
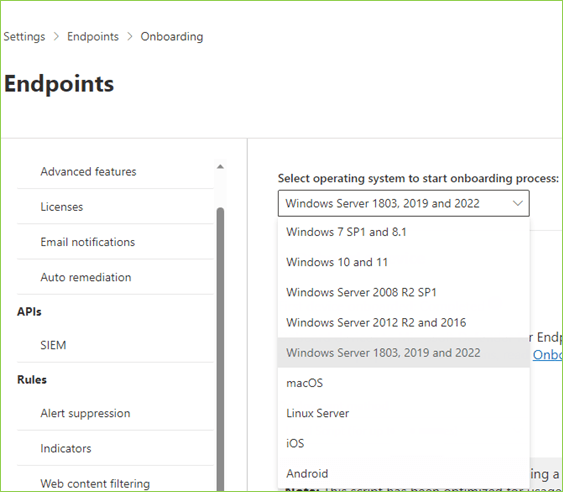
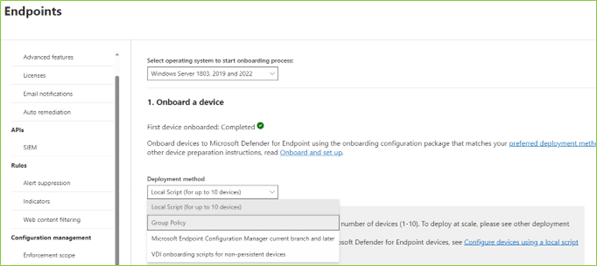
- Configure your security settings and preferences on the Security Copilot dashboard.
- Start monitoring and managing your data security with the service.
Microsoft Security Copilot is a powerful and easy-to-use service that can help you protect your data from cyber threats. It leverages the advanced capabilities of Microsoft 365 and Azure to provide a comprehensive and integrated data security solution. Try it today and see how it can enhance your data security. To learn more, click here.